iPhone 15 Rumors: Everything We're Hearing About Apple's Next Phone - CNET
Updated: 2022-12-31 13:00:00
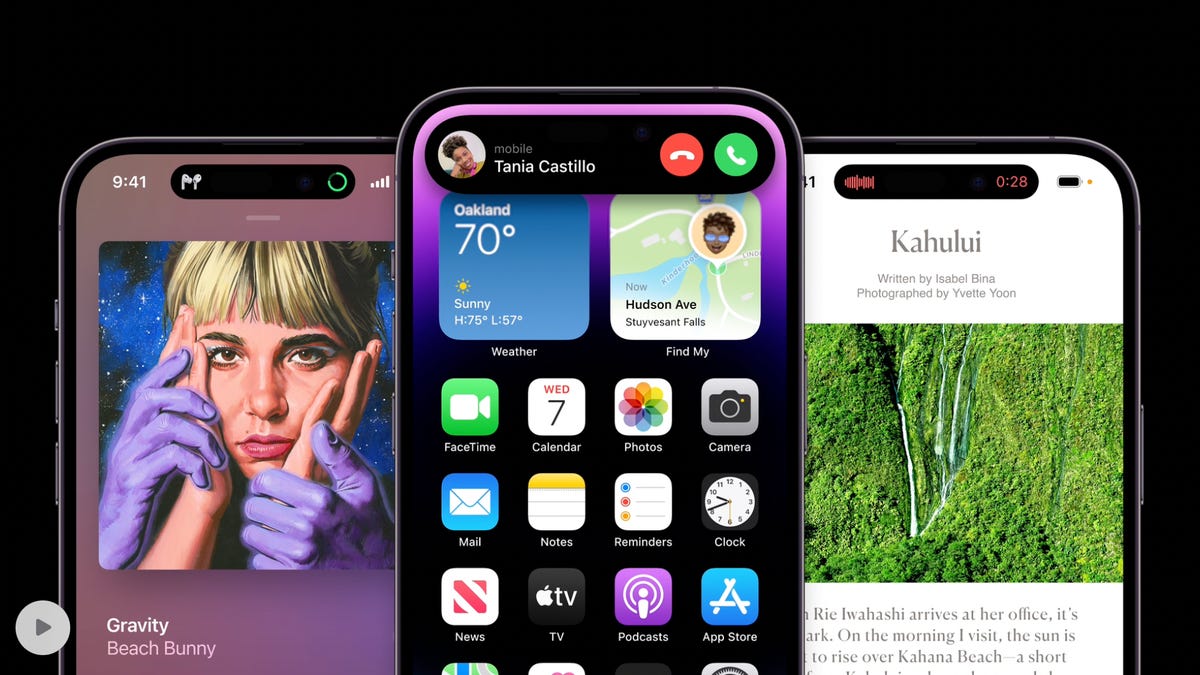 Our unofficial curtain-raiser on Apple's iPhone 15 series based on the most credible rumors circulating so far.
Our unofficial curtain-raiser on Apple's iPhone 15 series based on the most credible rumors circulating so far. Our unofficial curtain-raiser on Apple's iPhone 15 series based on the most credible rumors circulating so far.
Our unofficial curtain-raiser on Apple's iPhone 15 series based on the most credible rumors circulating so far. It'll be easier for people to opt out of Google's location tracking.
It'll be easier for people to opt out of Google's location tracking. Missions OSINT Law Enforcement OIG Advanced Missions Products Nfusion Mapper Advanced Solutions Academy Training Courses Blog Resources Events Careers Job Listings About You Benefits Life at Ntrepid About Leadership Locations Research Development Engineering Contact Contact Search What Is Open Source Intelligence OSINT Share this post Facebook Twitter LinkedIn Email 12 Feb February 12, 2019 What Is Open Source Intelligence OSINT d1webb 2021-03-17T08:34:51-05:00 Nfusion Open Source Intelligence , or OSINT is intelligence developed from sources that are free , public , and legal to access . This should not be confused with Open Source Software . OSINT is the opposite of many other forms of intelligence . Unlike sources of intelligence like spies , satellites , sensors , and hackers , OSINT
Missions OSINT Law Enforcement OIG Advanced Missions Products Nfusion Mapper Advanced Solutions Academy Training Courses Blog Resources Events Careers Job Listings About You Benefits Life at Ntrepid About Leadership Locations Research Development Engineering Contact Contact Search What Is Open Source Intelligence OSINT Share this post Facebook Twitter LinkedIn Email 12 Feb February 12, 2019 What Is Open Source Intelligence OSINT d1webb 2021-03-17T08:34:51-05:00 Nfusion Open Source Intelligence , or OSINT is intelligence developed from sources that are free , public , and legal to access . This should not be confused with Open Source Software . OSINT is the opposite of many other forms of intelligence . Unlike sources of intelligence like spies , satellites , sensors , and hackers , OSINT